This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
Recently, a YouTuber was assaulted at the GenCon gaming convention.
https://disneystarwarsisdumb.wordpress.com/2018/08/02/sjws-throw-the-first-punch-at-gencon/
http://boundingintocomics.com/2018/08/02/the-quarterings-jeremy-hambly-attacked-at-gencon-2018/
Apparently the assault was perpetrated because the YouTuber, the Quartering was a Trump supporter. Also apparently the perpetrator is the proprietor of a gaming store in New Haven CT. It is also apparent Jeremy Hambly is a nice guy and wants to seek justice through the legal system.
 As system get more complex they get more fragile. That is definitely the case when it comes to computer and information systems. I found that out again last Friday. Now as of now, I don’t know if what happened to my main computer is a hard drive failure or a corrupted update. At this point it’s hard to tell and it’s going to be some work to figure out what. My big mistake this time was not making a Windows 10 boot disk.
As system get more complex they get more fragile. That is definitely the case when it comes to computer and information systems. I found that out again last Friday. Now as of now, I don’t know if what happened to my main computer is a hard drive failure or a corrupted update. At this point it’s hard to tell and it’s going to be some work to figure out what. My big mistake this time was not making a Windows 10 boot disk.
https://www.xtremerain.com/fix-bad-system-config-info/
System failure can also be caused by malware and viruses though this has been less common as the security people have dealt with this sort of thing and if the data and files themselves are not wrecked, using a boot disk can get things running and work around the malware until things are running, anyway, here’s the week in ransomware.
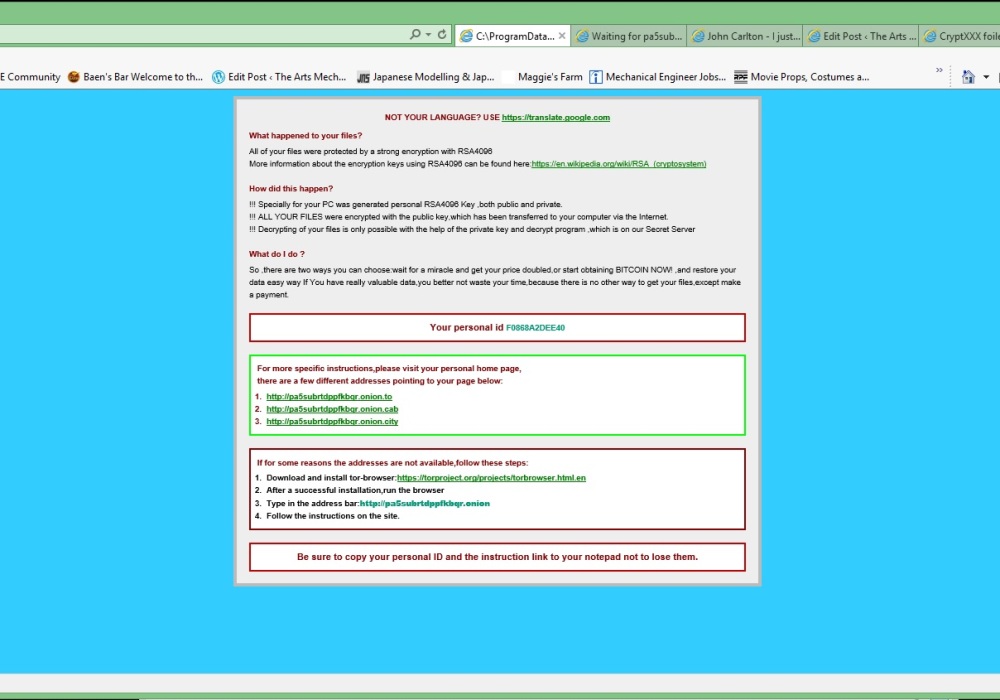
This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
Last week, I posted Karl Denninger’s rant on how MS and Apple had dropped the ball on computer security. The fact is that the current ransomware epidemic is the result of a four decade denial to understand that this problem even existed. Having had Windows 10 installed on the computer and using it for the last couple of months now I don’t see much effort to take things in the direction I think that the way things are going are going to force them to go.
Frankly this should have been considered a long time ago. We’ve all been spoiled and it’s not as if Hacking and computer security hasn’t been an issue. Yet none of the OS providers, including Linux seem to have invested much effort into creating the tools that make it easy to partition and protect drives and partitions from open access. That needs to change. There need to be tools installed and easily accessible to allow users to partition and separate data from the network access. These days computers are storing immense amounts of irreplaceable personal and corporate data that can be read or destroyed by any Tom Dick or Harry that gets access to the machine. It wasn’t that way before the PC, there’s no true reason, other than “we’ve always done it that way” to set up a system so that it’s not secure.
How might this be done? Well the old Unix system was set up so that individual spaces could be secured. If people want to know what can be done to partition and fence data so that it can be secured, that’s where I would start. Get a 1990’s vintage copy of BSD UNIX and play with how it works.
https://en.wikipedia.org/wiki/Berkeley_Software_Distribution
The fact is that unless resource access control becomes THE issue in the next round of OS updates, we will ALL be held for ransom. There’s no way the security firms can keep up with the infiltration efforts that the cybercriminals come up with and without being able to fence data, the users are going to be helpless.
This week in ransomware:
http://www.bleepingcomputer.com/news/security/the-week-in-ransomware-september-16-2016-stampado-locky-atom-and-more/
I was thinking about ATS systems and how they worked while cutting the lawn the other day and I had an insight about them that I don’t think that people appreciate. For a computer, there is no “maybe.” A computer is not a brain and the software program running defines everything as yes, or no.

This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
There is an old Roman saying; “Quis custodiet ipsos custodies?” It means, who will watch the watchers? It’s appropriate when considering the internet and the web. Heretofore the web standards and protocol development has been more or less a mutual agreement between interested parties who by and large had no real interest in doing anything that would create problems in real society. They just wanted to make their wonderful toy work. They were idealistic and didn’t really see the potentials of the dark side.

This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
Check out this archive of a search on twitter for “crypz.”

This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
I’ve been called an idiot in various venues by mostly it seems computer security types for this series and my insistence that more law enforcement is required. What these people don’t see is the bigger issues involved.

This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
The fact that they are young and inexperienced seems to work against them. They make mistakes. And get caught. The interesting thing is that, like a medieval castle under siege the dark net is most likely to break from the inside. What’s also amazing is that no matter how stupid the last guy was and how big the punishment, there’s always anew idiot ready and willing to step in and be the next guy on the “caught” list. One would think that the possibility of a lifetime relationship with “Bubba” and his friend and strict limitations on computer usage would be a huge deterrent. Apparently not.

This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
In this post we are going to take look inside the guts of a ransomware program. How this stuff comes about is unknown, but there are some clues. The key thing is that the malware relies on the TOR browser anonymity to do it’s work.
Thoughts on kayaking, science, and life
Articles and images about NYC history
Conservative thought and commentary
Exploring the world's greatest city: Geography & environment | Transportation & urban design | Art, culture & history
International Association of Ghost Gun Forensic Examiners
amiecus curiae - thoughts and writings from a friend of the courts
Just Another Loogie Hocked On The Information Super-Highway!
S blog featuring retro and vintage subjects of a great varitety
Innovation and Entrepreneurship
Established 2006 - 100+ NEW posts every year: Movie Locations, B-Grade Sights, Cycling Trips, Travel, Films, Railways, Foxes, Star Wars, J-League, Dining Out, Sport, LCFC.......
Helping people who have to say "now what?"
A regular interrogation of what Japanese "comics" are and are not Nicholas A. Theisen
Business Bullshit, Corporate Crap and other stuff from the World of Work
“He is a sane man who can have tragedy in his heart and comedy in his head.” - GK Chesterton
ISSN 2562-9948
World War II with Scale Models
History and Hardware of Warfare
The Art blog about the Old Masters and Contemporary Artists
Greatest American Painters
Human history becomes more and more a race between education and catastrophe.
Chronicling an ever-changing city through faded and forgotten artifacts
All about the 42 Ford GPW and related WW2 information.
"How were the military strategies in Germany influenced by World War One, and how did these strategies change throughout the course of the war?”
Speculative Fiction Book Reviews and Sundry
Games, civilizations, and the game of civilization.
A time traveler from the age of steam
Just a teenager blogging about everything Disney with a little bit of pixie dust, of course!
Swimming Is Our Passion
a maker, a teacher of making
Spaceflight History and Commentary
Electrostatic Dispersal Solutions
A world of.....'Leaky Leaks' and....."Likes" !!
This WordPress.com site is the bee's knees
Exploring History with the National Archives Special Media Division
Fresh hacks every day
Exploring Tokyo one place name at a time
Artist, author
Typography and Design in Science Fiction Movies
Anything Geekish Goes!
Precision Machining Technologies - Education in Manufacturing