This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
Here’s a blog post with a short history of ransomware.
17 years after the first ransomware malware was distributed, another strain was released but this time it was much more invasive and difficult to remove than its predecessor. In 2006, the Archiveus Trojan was released, the first ever ransomware virus to use RSA encryption. The Archiveus Trojan encrypted everything in the MyDocuments directory and required victims to purchase items from an online pharmacy to receive the 30-digit password.
June 2006 – the GPcode, an encryption Trojan which spread via an email attachment purporting to be a job application, used a 660-bit RSA public key.
2007
At the same time GP Code and it’s many variants were infecting victims, other types of ransomware circulated that did not involve encryption, but simply locked out users. WinLock displayed pornographic images until the users sent a $10 premium-rate SMS to receive the unlocking code.
2008
Two years after the initial GP Code virus was created, another variant of the same virus called GPcode.AK was unleashed on the public using a 1024-bit RSA key.
2011
Mid 2011 – The first large scale ransomware outbreak, and ransomware moves into the big time due to the use of anonymous payment services, which made it much easier for ransomware authors to collect money from their victims. There were about 30,000 new ransomware samples detected in each of the first two quarters of 2011.
July 2011 – During the third quarter of 2011, new ransomware detections doubled to 60,000.
2012
January 2012– The cybercrime ecosystem comes of age with Citadel, a toolkit for distributing malware and managing botnets that first surfaced in January 2012. Citadel makes it simple to produce ransomware and infect systems wholesale with pay-per-install programs allowing cybercriminals to pay a minimal fee to install their ransomware viruses on computers that are already infected by other malware. Due to the introduction of Citadel, ransomware infections surpassed 100,000 in the first quarter of 2012.
Cyber criminals begin buying crime kits like Lyposit—malware that pretends to come from a local law enforcement agency based on the computer’s regional settings, and instructs victims to use payment services in a specific country—for just a share of the profit instead of for a fixed amount.
March 2012 – Citadel and Lyposit lead to the Reveton worm, an attempt to extort money in the form of a fraudulent criminal fine. Reveton first showed up in European countries in early 2012. The exact “crime” and “law enforcement agency” are tailored to the user’s location. The threats are “pirated software” or “child pornography”. The user would be locked out of the infected computer and the screen be taken over by a notice informing the user of their “crime” and instructing them that to unlock their computer they must pay the appropriate fine using a service such as Ukash, Paysafe or MoneyPak.
April 2012 – Urausy Police Ransomware Trojans are some of the most recent entries in these attacks and are responsible for Police Ransomware scams that have spread throughout North and South America since April of 2012.
July 2012– Ransomware detections increase to more than 200,000 samples, or more than 2,000 per day.
November 2012– Another version of Reveton was released in the wild pretending to be from the FBI’s Internet Crime Complaint Center (IC3). Like most malware, Reveton continues to evolve.
2013
July 2013 – A version of ransomware is released targeting OSX users that runs in Safari and demands a $300 fine. This strain does not lock the computer or encrypt the files, but just opens a large number of iframes (browser windows) that the user would have to close. A version purporting to be from the Department of Homeland Security locked computers and demanded a $300 fine.
July 2013 –Svpeng: This mobile Trojan targets Android devices. It was discovered by Kaspersky in July 2013 and originally designed to steal payment card information from Russian bank customers. In early 2014, it had evolved into ransomware, locking the phones displaying a message accusing the user of accessing child pornography. By the summer of 2014, a new version was out targeting U.S. users and using a fake FBI message and requiring a $200 payment with variants being used in the UK, Switzerland, India and Russia. According to Jeremy Linden, a senior security product manager for Lookout, a San Francisco-based mobile security firm, 900,000 phones were infected in the first 30 days.
August 2013– A version masquerading as fake security software known as Live Security Professional begins infecting systems.
September 2013 –CryptoLocker is released. CryptoLocker is the first cryptographic malware spread by downloads from a compromised website and/or sent to business professionals in the form of email attachments that were made to look like customer complaints controlled through the Gameover ZeuS botnet which had been capturing online banking information since 2011.
Cryptolocker uses a 2048-bit RSA key pair, uploaded to a command-and-control server, and used it to encrypt files with certain file extensions, and delete the originals. It would then threaten to delete the private key if payment was not received within three days. Payments initially could be received in the form of Bitcoins or pre-paid cash vouchers.
With some versions of CryptoLocker, if the payment wasn’t received within three days, the user was given a second opportunity to pay a much higher ransom to get their files back. Ransom prices varied over time and with the particular version being used. The earliest CryptoLocker Payments could be made by CashU, Ukash, Paysafecard, MoneyPak or Bitcoin. Prices were initially set at $100, €100, £100, two Bitcoins or other figures for various currencies.
November 2013 – The ransom changes. The going ransom was 2 Bitcoins or about $460, if they missed the original ransom deadline they could pay 10 Bitcoins ($2300) to use a service that connected to the command and control servers. After paying for that service, the first 1024 bytes of an encrypted file would be uploaded to the server and the server would then search for the associated private key.
Early December 2013 – 250,000 machines infected. Four Bitcoin accounts associated with CryptoLocker found that 41,928 Bitcoins had been moved through those four accounts between October 15 and December 18. Given the then current price of $661, that would represent more than $27 million in payments received, not counting all the other payment methods.
Mid December 2013 – The first CryptoLocker copycat software emerges, Locker, charging users $150 to get the key, with money being sent to a Perfect Money or QIWI Visa Virtual Card number.
Late December 2013 –CryptoLocker 2.0– Despite the similar name, CryptoLocker 2.0 was written using C# while the original was in C++ so it was likely done by a different programming team. Among other differences, 2.0 would only accept Bitcoins, and it would encrypt image, music and video files which the original skipped. And, while it claimed to use RSA-4096, it actually used RSA-1024. However, the infection methods were the same and the screen image very close to the original.
Also during this timeframe, CryptorBit surfaced. Unlike CryptoLocker and CryptoDefense which only targets specific file extensions, CryptorBit corrupts the first 212 or 1024 bytes of any data file it finds. It also seems to be able to bypass Group Policy settings put in place to defend against this type of ransomware infection. The cyber gang uses social engineering to get the end-user to install the ransomware using such devices as a rogue antivirus product. Then, once the files are encrypted, the user is asked to install the Tor Browser, enter their address and follow the instructions to make the ransom payment – up to $500 in Bitcoin. The software also installs cryptocoin mining software that uses the victim’s computer to mine digital coins such as Bitcoin and deposit them in the malware developer’s digital wallet.
2014
February 2014 – CryptoDefense is released. It used Tor and Bitcoin for anonymity and 2048-bit encryption. However, because it used Windows’ built-in encryption APIs, the private key was stored in plain text on the infected computer. Despite this flaw, the hackers still managed to earn at least $34,000 in the first month, according to Symantec.
April 2014 – The cyber criminals behind CryptoDefense release an improved version called CryptoWall. While largely similar to the earlier edition, CryptoWall doesn’t store the encryption key where the user can get to it. In addition, while CryptoDefense required the user to open an infected attachment, CryptoWall uses a Java vulnerability. Malicious advertisements on domains belonging to Disney, Facebook, The Guardian newspaper and many others led people to sites that were CryptoWall infected and encrypted their drives. According to an August 27 report from Dell SecureWorks Counter Threat Unit (CTU): “CTU researchers consider CryptoWall to be the largest and most destructive ransomware threat on the Internet as of this publication, and they expect this threat to continue growing.” More than 600,000 systems were infected between mid-March and August 24, with 5.25 billion les being encrypted. 1,683 victims (0.27%) paid a total $1,101,900 in ransom. Nearly 2/3 paid $500, but the amounts ranged from $200 to $10,000.
Koler.a: Launched in April, this police ransom Trojan infected around 200,000 Android users, 3⁄4 in the US, who were searching for porn and wound up downloading the software. Since Android requires permission to install any software, it is unknown how many people actually installed it after download. Users were required to pay $100 – $300 to remove it.
May 2014 – A multi-national team composed of government agencies managed to disable the Gameover ZeuS Botnet. The U.S. Department of Justice also issued an indictment against Evgeniy Bogachev who operated the botnet from his base on the Black Sea.
iDevice users in Australia and the U.S. started seeing a lock screen on their iPhones and iPads saying that it had been locked by “Oleg Pliss” and requiring payment of $50 to $100 to unlock. It is unknown how many people were affected, but in June the Russian police arrested two people responsible and reported how they operated. This didn’t involve installing any malware, but was simply a straight up con using people’s naiveté and features built into iOS. First people were scammed into signing up for a fake video service that required entering their Apple ID. Once they had the Apple ID, the hackers would create iCloud accounts using those ID’s and use the Find My Phone feature, which includes the ability to lock a stolen phone, to lock the owners out of their own devices.
July 2014 – The original Gameover ZeuS/CryptoLocker network resurfaced no longer requiring payment using a MoneyPak key in the GUI, but instead users must to install Tor or another layered encryption browser to pay them securely and directly. This allows malware authors to skip money mules and improve their bottom line.
Cryptoblocker– July 2014 Trend Micro reported a new ransomware that doesn’t encrypt files that are larger than 100MB and will skip anything in the C:\Windows, C:\Program Files and C:\Program Files (x86) folders. It uses AES rather than RSA encryption.
On July 23, Kaspersky reported that Koler had been taken down, but didn’t say by whom.
August 2014 – Symantec reports crypto-style ransomware has seen a 700 percent-plus increase year-over-year.
SynoLocker appeared in August 2014. Unlike the others which targeted end-user devices, this one was designed for Synology network attached storage devices. And unlike most encryption ransomware, SynoLocker encrypts the files one by one. Payment was 0.6 Bitcoins and the user has to go to an address on the Tor network to unlock the files.
This was discovered midsummer 2014 and Fedor Sinitisyn, a security researcher for Kaspersky. Early versions only had an English language GUI, but then Russian was added. The first infections were mainly in Russia, so the developers were likely from an eastern European country, not Russia, because the Russian security services quickly arrest and shut down any Russians hacking others in their own country.
Late 2014 –TorrentLocker– According to iSight Partners, TorrentLocker “is a new strain of ransomware that uses components of CryptoLocker and CryptoWall but with completely different code from these other two ransomware families.” It spreads through spam and uses the Rijndael algorithm for file encryption rather than RSA-2048. Ransom is paid by purchasing Bitcoins from specific Australian Bitcoin websites.
2015
Early 2015 – CrytoWall takes off, and replaces Cryptolocker as the leading ransomware infection.
April 2015 – CrytoLocker is now being localized for Asian countries. There are attacks in Korea, Malaysia and Japan.
May 2015 – It’s heeere. Criminal ransomware-as-a-service has arrived. In short, you can now go to this TOR website “for criminals by criminals”, roll your own ransomware for free, and the site takes a 20% kickback of every Bitcoin ransom payment. Also in May 2015 a new strain shows up that is called Locker and has been infecting employee’s workstations but sat there silently until midnight May 25, 2015 when it woke up. Locker then started to wreak havoc in a massive way.
May 2015 – New “Breaking Bad-themed ransomware” gets spotted in the wild. Apart from the Breaking Bad theme, CryptoLocker.S is pretty generic ransomware. It is surprising how fast ransom Trojans have developed. A year ago every new strain was headline news, now it’s on page 3. This version grabs a wide range of data files, encrypts it using a random AES key which then is encrypted using a public key.
June 2015 – SANS InfoSec forum notes that a new version of CryptoWall 3.0 is in the wild, using resumes of young women as a social engineering lure: “resume ransomware”.
June 2015 – The FBI, through their Internet Crime Complaint Center (IC3), released an alert on June 23, 2015 that between April 2014 and June 2015, the IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. Ransomware gives cybercriminals almost 1,500% return on their money.
July 2015 – KnowBe4 released the first version of their Ransomware Hostage Rescue Manual. Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist.
July 2015 – An Eastern European cybercrime gang has started a new TorrentLocker ransomware campaign where whole websites of energy companies, government organizations and large enterprises are being scraped and rebuilt from scratch to spread ransomware using Google Drive and Yandex Disk.
July 2015 – Security researcher Fedor Sinitsyn reported on the new TeslaCrypt V2.0. This family of ransomware is relatively new, it was first detected in February 2015. It’s been dubbed the “curse” of computer gamers because it targets many game-related file types.
September 2015 – An aggressive Android ransomware strain is spreading in America. Security researchers at ESET discovered the first real example of malware that is capable to reset the PIN of your phone to permanently lock you out of your own device. They called it LockerPin, and it changes the infected device’s lock screen PIN code and leaves victims with a locked mobile screen, demanding a $500 ransom.
September 2015 – The criminal gangs that live off ransomware infections are targeting Small Medium Business (SMB) instead of consumers, a new Trend Micro Analysis shows. The reason SMB is being targeted is that they generally do not have the same defenses in place of large enterprise, but are able to afford a 500 to 700 dollar payment to get access to their files back.
The Miami County Communication Center’s administrative computer network system was compromised with a CryptoWall 3.0 ransomware infection which locked down their 911 emergency center. They paid a 700 dollar Bitcoin ransom to unlock their files.
October 2015 – A new ransomware strain spreads using remote desktop and terminal services attacks. The ransomware is called LowLevel04 and encrypts data using RSA-2048 encryption, the ransom is double from what is the normal $500 and demands four Bitcoin. Specifically nasty is how it gets installed: brute force attacks on machines that have Remote Desktop or Terminal Services installed and have weak passwords.
October 2015 – The nation’s top law enforcement agency is warning companies that they may not be able to get their data back from cyber criminals who use Cryptolocker, Cryptowall and other malware without paying a ransom. “The ransomware is that good,” said Joseph Bonavolonta, the Assistant Special Agent in Charge of the FBI’s CYBER and Counterintelligence Program in its Boston office. “To be honest, we often advise people just to pay the ransom.”
October 2015 – Staggering CryptoWall Ransomware Damage: 325 Million Dollar. A brand new report from Cyber Threat Alliance showed the damage caused by a single criminal Eastern European cyber mafia. The CTA is an industry group with big-name members like Intel, Palo Alto Networks, Fortinet and Symantec and was created last year to warn about emerging cyber threats.
November 2015 – CryptoWall v4.0 released and displays a redesigned ransom note, new filenames, and now encrypts a file’s name along with its data. In summary, the new v4.0 release now encrypts file names to make it more difficult to determine important files, and has a new HTML ransom note that is even more arrogant than the last one. It also gets delivered with the Nuclear Exploit Kit, which causes drive-by infections without the user having to click a link or open an attackment (sic).
November 2015 – A Ransomware news roundup reports a new strain with a very short 24-hour deadline, researchers crack the Linix.Encover strain and British Parliament computers get infected with ransomware.
December 2015 – A Kaspersky reports that ransomware is doubling year over year, and Symantec reports that TeslaCrypt attacks moved from 200 to 1,800 a day.
Here is a graph made by the folks at Bromium over the years 2013-2015 as an illustration:
2016
January 2016 – First Javascript-only Ransomware-as-a-Service Discovered, Cybercrime has piggybacked on the extremely successful SaaS model and several strains of Ransomware-as-a-Service (RaaS) like TOX, Fakben and Radamant have appeared in 2015. However, a new strain called Ransom32 has a twist: it was fully developed in JavaScript, HTML and CSS which potentially allows for multi-platform infections after repackaging for Linux and MacOS X. Using JavaScript brings us one step closer to the “write-once-infect-all” threat, which is something to be aware of.
January 2016 – A stupid and damaging new ransomware strain called 7ev3n encrypts your data and demands 13 bitcoins to decrypt your files. A 13 bitcoin [almost $5,000] ransom demand is the largest we have seen to date for this type of infection, but that is only just one of the problems with this ransomware. In addition to the large ransom demand, the 7ev3n crypto-ransom malware also does a great job trashing the Windows system that it was installed on. DarkReading reports on a Big Week In Ransomware.
February 2016 – Ransomware criminals infect thousands with a weird WordPress hack. An unexpectedly large number of WordPress websites have been mysteriously compromised and are delivering the TeslaCrypt ransomware to unwitting end-users. Antivirus is not catching this yet.
February 2016 – It’s Here. New Ransomware Hidden In Infected Word Files. It was only a matter of time, but some miscreant finally did it. There is a new ransomware strain somewhat amateurishly called “Locky”, but this is professional grade malware. The major headache is that this flavor starts out with a Microsoft Word attachment which has malicious macros in it, making it hard to filter out. Over 400,000 workstations were infected in just a few hours, data from Palo Alto Networks shows. Behind Locky is the deadly Dridex gang, the 800-pound gorilla in the banking Trojan racket.
March 2016 – MedStar receives a massive ransomware demand. The MedStar Hospital Chain was hit with ransomware and has received a digital ransom note. A Baltimore Sun reporter has seen a copy of the cybercriminal’s demands. “The deal is this: Send 3 bitcoins — $1,250 at current exchange rates — for the digital key to unlock a single infected computer, or 45 bitcoins — about $18,500 — for keys to all of them.”
April 2016 – News came out about a new type of ransomware that does not encrypt files but makes the whole hard disk inaccessible. As if encrypting files and holding them hostage is not enough, cybercriminals who create and spread crypto-ransomware are now resorting to causing blue screen of death (BSoD) and putting their ransom notes at system startup—as in, even before the operating system loads. It’s called Petya and clearly Russian.
April 2016 – The Ransomware That Knows Where You Live. It’s happening in the UK today, and you can expect it in America tomorrow [correction- it’s already happening today]. The bad guys in Eastern Europe are often using the U.K. as their beta test area, and when a scam has been debugged, they go wide in the U.S. So here is what’s happening: victims get a phishing email that claims they owe a lot of money, and it has their correct street address in the email. The phishing emails tell recipients that they owe money to British businesses and charities when they do not.
April 2016 – Hello mass spear phishing, meet ransomware! Ransomware is now one of the greatest threats on the internet. Also, a new ransomware strain called CryptoHost was discovered, which claims that it encrypts your data and then demands a ransom of .33 bitcoins to get your files back (~140 USD at the current exchange rate) . These cybercrims took a shortcut though, your files are not encrypted but copied into a password protected RAR archive .
April 2016 – The Future of Ransomware: CryptoWorms? Cisco’s Talos Labs researchers had a look into the future and described how ransomware would evolve. It’s a nightmare. They created a sophisticated framework for next-gen ransomware that will scare the pants off you. Also, a new strain of ransomware called Jigsaw starts deleting files if you do not pay the ransom.
April 2016 – Ransomware On Pace To Be A 2016 $1 Billion Dollar Business. CNN Money reports about new estimates from the FBI show that the costs from so-called ransomware have reached an all-time high. Cyber-criminals collected $209 million in the first three months of 2016 by extorting businesses and institutions to unlock computer servers. At that rate, ransomware is on pace to be a $1 billion a year crime this year.
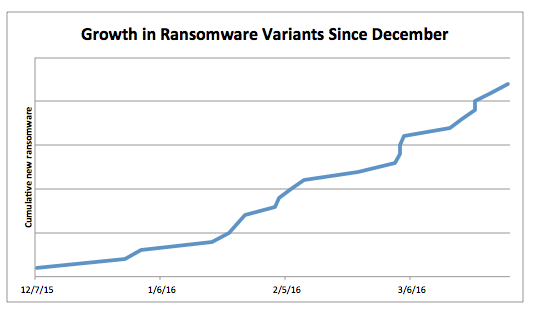
Here is a graph created by the folks of Proofpoint which illustrates the growth of new strains in Q1, 2016:
Late April 2016 – Scary New CryptXXX Ransomware Also Steals Your Bitcoins. Now here’s a new hybrid nasty that does a multitude of nefarious things. A few months ago the 800-pound Dridex cyber gang moved into ransomware with Locky, and now their competitor Reveton follows suit and tries to muscle into the ransomware racket with an even worse criminal malware multitool. At the moment CryptXXX spreads through the Angler Exploit Kit which infects the machine with the Bedep Trojan, which in its turn drops information stealers on the machine, and now ads professional grade encryption adding a .crypt extension to the filename. Here is a blog post that looks at the first 4 month of 2016 and describes an explosion of new strains of ransomware.
https://blog.knowbe4.com/a-short-history-evolution-of-ransomware
What we are seeing here is an explosion. And an escalation of ever more pressure on users to pay, by ever more nasty ways to trash data. This is a real problem. Of course I’m beginning to sound like a broken record, but the number speak for themselves. The outlook is not good for the rest of us. Here are some videos.
The pattern of escalation is continuing. and getting more stupid. Putting ransomware software out for people to just click and start using? Franchising the stuff. It’s too bad that Faginy is not a real crime. This is just stupid on all sorts of levels. If nothing is done to create a deterrent at this point, it’s going to be ugly. The latest reports I’ve seen say that as many as 20% of victims are shut down. Many even if they pay the ransom. This must stop.
The #Ransomware twitter page:
https://twitter.com/hashtag/Ransomware?src=hash