This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
Maybe the bigger question is why don’t seem to get that they have a real problem. Look the real world is having a real problem with TOR based crime from malware and ransomware crooks. The reason that these people are able to get away with what they do is that they can hide behind the anonymity that TOR provides. Which lowers the risk side of the risk/reward equation. Which is leading to more individuals and institutions being hit. Look, the people being hit now aren’t big corporations, they are frequently people like the woman in the local senior center that got hit with the child porn ransomware recently. Or just people who accidently click on the wrong link in an email.
The fact is that these people need to be shut down, hard. I’m going to reiterate the fact that these people are encrypting medical data in hospitals. There’s also the fact that the reasonable user shouldn’t have to be constantly afraid that merely using the internet will allow some clown to wreck their lives. In the long term, everybody has an interest in keeping the internet safe for users. That’s especially true for those who want to keep government intrusion to a minimum.
Consider this, this woman developer at TOR can’t understand why the FBI might just want to talk to her. She obviously doesn’t pay too much attention to the news in her own profession, let alone the news in general. Let me put it this way, hitting hospitals is a great way to attract law enforcement attention.
She claims that there have been many phone calls from FBI to her parents’ home requesting Isis to contact them.
In response, Isis has asked her lawyer to get in touch with the FBI agent who contacted her.
Recently,the Tor developer has published a blog accusing the FBI of harassing her for the last six months.
The Tor Developer and the FBI
It started when an FBI agent Mark Burnett turned up at Isis’ parents’ home last November.
On finding no one at home, he left behind a card (with an additional phone number) asking the Tor developer to contact him.
Given the fact that FBI is interested in anything that is related to Tor, Isis quickly involved her lawyer who requested that FBI should direct all questions to Isis and her family through him.
The FBI agent on the other end of the line quickly agreed and informed the lawyer that he would call back in five minutes’ time.
However, in the call made by Mark Burnett five minutes later, he expressed the opinion that he did not believe that the lawyer represented Isis.
He also added that though a phone call from the Tor developer would suffice, the FBI would be only too glad to meet her in person.
Burnett had also warned the lawyer that they would ask her questions directly in case they ran into her on the street.
The Tor developer and her lawyer discussed the range of topics that FBI would want to know about, including the Carnegie Mellon University attacks on Tor, request for backdoor entry into a software package, issuance of a subpoena to someone else, etc., but are clueless.
It was around the same time that Isis was making arrangements to move into Germany permanently.
http://www.ibtimes.co.uk/tor-developer-isis-agora-lovecruft-publicly-accuses-fbi-harassment-1558607
At this point it looks like Ms. Lovecruft should be served with a subpoena and possibly be extradited back to the US. She’s already got an attorney, good, but at some point she needs to talk to these people. Look, real people are getting hurt here. There’s a limit to pointless moralizing when others are losing their rights as a result of your work.
https://en.wikipedia.org/wiki/The_Tor_Project,_Inc
https://blog.torproject.org/blog/tor-misused-criminals
https://blog.torproject.org/blog/statement-tor-project-re-courts-february-23-order-us-v-Farrell
It looks like the government it trying to do things the hard way. Which is good, because sometime the hard way is the only way to get the job done. The thing is though is that the government shouldn’t have to. The TOR people seemed to have no trouble finding, doxxing and expelling the Carnegie Mellon people from the network, they can’t police the bad actors themselves?
http://gizmodo.com/attack-on-tor-has-likely-stripped-users-of-anonymity-1613247621
http://gizmodo.com/judge-confirms-carnegie-mellon-hacked-tor-and-provided-1761191933
http://gizmodo.com/report-claims-fbi-paid-carnegie-mellon-university-1m-t-1742089144
TOR seemed so proud that they stopped the “intrusion” from the government. Yet the extortion schemes, drug dealing to kids and the rest are allowed to go on under the protection of some unknown right to privacy. But what about other people’s right. Don’t I have a certain right to my data that was encrypted? I didn’t ask for somebody to encrypt my data and then demand ransom. How was MY privacy and security rights maintained by TOR’s desire to maintain anonymity.
Here’s an open question to TOR. How are you people NOT responsible for allowing the kind of thing that happened to me to continue for years? And going forward, are you willing to turn the bad apples in to maintain the anonymity of the network? Because if you cannot police the network, it’s going to be destroyed. How long does TOR continue to enable bad behavior before they become bad actors themselves? It seems to me as if they are dangerously close to that line already.
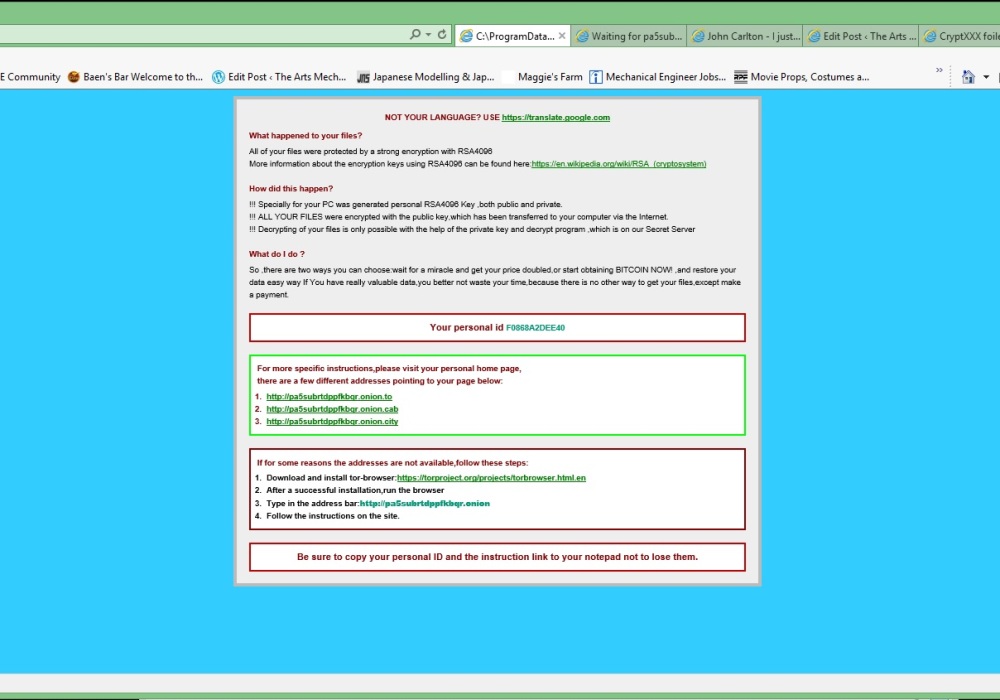
Here’s a proposal. Tor puts up a complaint forum where people can report things like the ransomware that I got. TOR goes to the node in the message and kills it, then sends a message that they have 24 hours to turn cease and desist and turn over the keys to the files they encrypted or they get doxxed and turned over to law enforcement. That way the anonymity of the network can be maintained. Look I just want my pictures back, no harm, no foul. But this can’t continue or there is going to be real consequences.
Well hey, it’s not as if they used gender specific insults or something actually *heinous*. /s
LikeLiked by 1 person
You’re blaming the gun, I mean TOR, for the misbehavior of people. You want to weaken TOR, which will shift the balance of power in favor of the group who kills people if they choose to carry self-defense guns into nightclubs. Encryption has military applications, and you want to infringe its use by good people.
LikeLike
TOR isn’t a gun. It’s service, not a product. Service providers have different rules and regulations than manufactures do. I’m fairly knowledgeable on how product liability and testing work as part of my work and I discussed the issues with TOR with friend who is a retired high level executive in charge of transportation services and the laws surrounding them. We went back and forth and when I mentioned that TOR was responsible for Routing a switch went off and, yes TOR is Liable for users who are breaking the law. In fact their funding legislation confirms this. If TOR provides some mechanism for redress, well I get my files back and that is the end. If they don’t then I will take other measures. What I’m thinking of doing and the approaches I use I’m not going to say. Let’s just say that I have multiple approaches and directions. And I want to stop BAD people from hiding behind encryptions services paid for by the government for their purposes and preying on all and sundry.
LikeLike
Government accurately notices that cryptography has military utility, and contrary to 2A regulates it as a munition for export under ITAR. I consider “rights” to be civilizational-level notes about terrible past policy mistakes. ‘Get serious about removing any of these rights, and you *will* produce a genocide.’ I don’t think the questions of who owns the computers TOR runs on and is it a service are important relative to 2A rights, which exist to prevent genocides.
Your screenshot shows you using Windows, which is about as good a defense against computer viruses as hiding in the bathroom is against a spree killer. In both cases there exists an inexpensive defense that actually works, and doesn’t infringe others’ rights: switch to Linux, carry a handgun everywhere. But instead, you want more control of arms? This puts minorities in a weaker position vs. those who oppress them, who numerically are overwhelmingly government employees.
If a murderer shoots someone, the government helps the victim’s survivors steal money from the gun manufacturer. The current behavior of product liability is wrong, and so extending it to TOR is also wrong.
LikeLiked by 1 person
TOR is Corporation in the State of Massachusetts providing internet services. As such they are subject to the laws of the State of Massachusetts and the United States of America. This kind of extortion activity is covered by those laws. As is the responsibility of service providers to turn in who use their service for criminal uses. This is reinforced by the funding legislation that is used to fund TOR. This activity has gone on for a significant amount of time and has reached epidemic and global proportions. Somehow TOR seems unwilling or unable to work to stop this. The deeper I reach into this the worse it gets.
LikeLike
However, you think encryption of military utility is *not* subject to protection against infringement due to the 2A, which is *not* one of the highest laws of the land? Please do list out all the steps in your legal argument, because I’m just not following it.
LikeLiked by 1 person
Just fyi your brief synopsis of Isis Lovecruft’s events which transpired with the FBI is not factually correct, and why it is in block quotes when it is most definitely not a quote idk…and why you would introduce the entire story with “this woman developer” as if because of her gender, she is somehow different than any other developer? Regardless, I know your pissed about losing your files, even though they aren’t lost, they will just being held ransom…so I guess it really depends on how much those files are really worth to you. I will even help you going forward http://www.welivesecurity.com/2013/12/12/11-things-you-can-do-to-protect-against-ransomware-including-cryptolocker/ here is a link to protecting yourself in the future…blaming a government funded piece of software and trying to hold them accountable is more slimy than the guys who locked your files….a progressive individual would come up with a solution, not point fingers….I’d hate to be one of your employees, considering you are a manager or boss, you would be horrible to work for….I have a suggestion, come up with your own ground breaking software that can help alleviate such risks instead of pointing fingers at people….people who do…do people who don’t…blame
LikeLike
You really shouldn’t run to conclusions. I put the text describing MS Lovecruft’s interactions in a block quote because I quoted the text, link below it. As for being a boss, My one employee is me and he hates me because I’m a slave driver. And I’ve seen a TON of stuff about security and USED a TON more. I’ve been hit, badly by malware before. Is it logical though to expect every individual to become security experts? I missed ONE update apparently and that was all it took. As for Tor being responsible, there is a large difference between being responsible and being liable. I actually discussed this at length with an expert in these matters and In certain area of the commerce laws and the law funding Tor, if Tor is managing the network and providing router and terminal services, they may be held liable for damages as result of actions of people using Tor, it that activity is criminal and Tor knew about it and did not take steps to shut it down.
LikeLike
More coming on that.
LikeLike