This is the first in what is going to be series of posts on cybercrime, the web and ransomeware in particular. I hope that I get my files back, but I’m not counting on it. In any case I’m going to hit them with everything I can and bring this stuff to the light as much as possible.
This is a post series on cyber crime. For more posts click here or the cybercrime tag below.
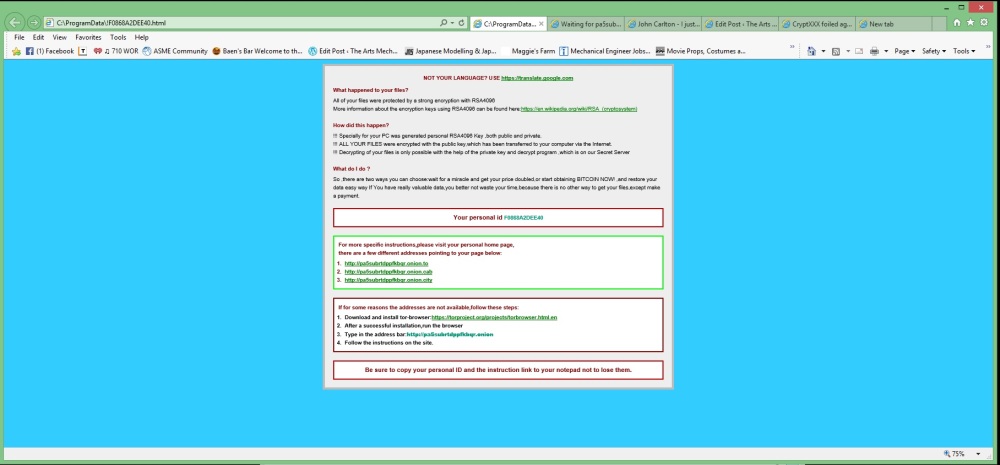
I was stupid. I let a executable make changes to my hard drive without knowing what it was. Well to be honest, once the dialog box was running I wasn’t given much choice. I couldn’t interrupt the process and close the dialog box. In any case the ransomware did the nasty across my files encrypting almost all of them. It’s frightening when your background goes black and you see this:
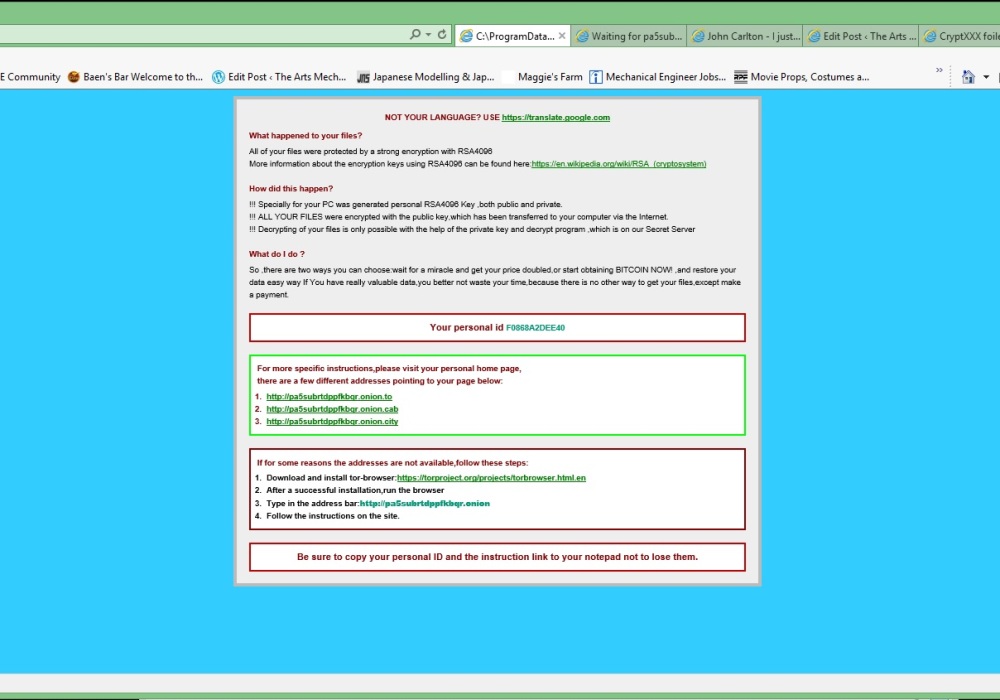
@@@@@@@ NOT YOUR LANGUAGE? USE https://translate.google.com
@@@@@@@ What happened to your files ?
@@@@@@@ All of your files were protected by a strong encryption with RZA4096
@@@@@@@ More information about the en-Xryption keys using RZA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)@@@@@@@ How did this happen ?
@@@@@@@ !!! Specially for your PC was generated personal RZA4096 Key , both publik and private.
@@@@@@@ !!! ALL YOUR FILES were en-Xrypted with the publik key, which has been transferred to your computer via the Internet.
@@@@@@@ !!! Decrypting of your files is only possible with the help of the privatt key and de-crypt program , which is on our Secret Server@@@@@@@ What do I do ?
@@@@@@@ So , there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! , and restore your data easy way
@@@@@@@ If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment
Your personal ID: F0868A2DEE40For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1 -http: //pa5subrtdppfkbqr.onion.to
2 -http: //pa5subrtdppfkbqr.onion.cab
3 -http: //pa5subrtdppfkbqr.onion.cityIf for some reasons the addresses are not available, follow these steps:
1 – Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2 – After a successful installation, run the browser
3 – Type in the address bar -http://pa5subrtdppfkbqr.onion
4 – Follow the instructions on the siteBe sure to copy your personal ID and the instruction link to your notepad not to lose them.
Cry and panic. Then do what I always do and evaluate the damage and plan recovery. There’s no point in being angry and upset for very long. It doesn’t help. Google the problem and look for solutions. And don’t worry, you haven’t lost as much as it first seems.
The problem is that while many crucial files are backed up, my resume and the like, some of the backups are on old computers. So I’m not dead in the water. I also had a fair amount of copies of my pics and videos on the old computer. Which is a good thing. See the key vulnerability of any encryption scheme is the fact that the original has to be clear. if somebody has an original copy in clear, encryption doesn’t work. So even if you have some files backed up some place you should be able to get the key to all of them. Still this is more than a nuisance for the home user or small business.
So what should you do? I’m going to assume that you were as stupid as I was and had a big chunk of your stuff in open folders on one computer. At this point you can pay the Danegeld and hope or take stock, find out just how bad it is. Break it down to got to have mission necessary files, good to have but not critical and files you don’t care about. If you don’t have backups of the first category, pay. $500 is too small an amount to take the risk. If the loss in the second category, it’s iffy. If the majority of the loss in the third category, who cares.
The other thing to remember is that you are not alone. There are services out there that do recovery from this. And even if the version you got hit with hasn’t been keyed yet, it soon will be.
http://esupport.trendmicro.com/en-us/default.aspx
So there are people, even though you will never meet, helping you for no other motivation than they can make money helping people. Then there are the organizations who don’t like losing data that have every interest in making sure that date gets restored. So all is not lost. Even if the decryption isn’t available now, it more than likely will be soon.
There’s also the fact that the greatest weakness in encryption is that there has to be retrievable information and access to clear copy means that the key is right there. So it’s better to think of your files as being stored for a while, not gone. Even if they are gone, well, you have to clean up from time to time anyway. In a year you won’t care. Life goes on.
In my case, the mission critical files were my resume, which was backed up on two different memory sticks and another computer and my Solidworks files, which the malware didn’t even see. It was amazing to see my part and assembly files still there unencrypted amongst the encrypted PDF printouts. Frankly, as far as virus’ go this was fairly benign. It even seems to have deleted itself more or less once it was done. Which I’m amazed to figure out why the malware people took this long to figure out that having an executable stay resident is not a very good idea because the file can be decompiled and all sorts of interesting stuff found out about the creators.
So what can you do to prevent this sort of thing. Realistically, not much. Yes you can catch most of it with firewalls and security software, but there’s always that stupid mistake, those bad ads that never go away unless you push the button, the strange dialog box that lockup your computer. You have to be alert, but in the end there will be a slip up. The best thing you can do is make backups of your mission critical files, store your images off drive and keep copies on plug in drives. That way when the mistake happens you don’t have to panic. You may not save everything, but that’s not all bad.
Now as to whether the cyber criminals will ever pay any penalty. It’s hard to tell.
I would like to believe that these people are not as anonymous as they would like to believe, but that’s just dreaming. The only thing you can do is not pay and hope that they stop because they can’t make any money. but that’s not going to happen soon. In any case I don’t have $500 to pay them right now, so for me the point is moot. Be careful and don’t let this happen to you.
Reblogged this on PenneyVanderbilt and commented:
I thought all the stuff at the beginning was because I physically live in France, BUT SO PISSED OFF AT ALWAYS GETTING STUFF IN FRENCH
LikeLike
I wanna see an OS extension that will detect any attempt to access and re-write so many files and stop the process doing it.
LikeLike
Program unknown, controlled by persons unknown, has confiscated your files. The sum total of what you about the program and the persons behind it is the picture on your screen. Copycat attacks are a popular strategy; the googles cannot connect this attack with previous attacks, because they can’t prove who launched this particular attack and what behaviors of the program and the attackers might have changed.
What does the attack suggest about their respect for your property and autonomy? What data leads you to believe that if you pay the money demanded, you will receive the unencrypt promised instead of a larger demand? How do you know they will only put the tip in, and if you just put on the handcuffs and get in the car quietly, they will release you unharmed after they have had their fun? How do you know there really is work in the East?
One defense you can adopt, today, is to switch to Linux.
LikeLike
Well a switch to Linux is not possible at this time, though it’s not a bad thing for some things. As for whether they actually give me the key if I pay, since I don’t have $500 right now, the question is moot. But if I did pay and the screw up, which they already have, they are done. They may be anonymous for now, but the very nature of the internet is such that they cannot remain anonymous if somebody wants them hard enough. And the FBI already wants them hard enough, thanks to all those hospitals getting hit. I’m thinking that they never realized that they were one missed dialysis session, surgery, drug tolerance, toxicity study or whatever from a second degree murder charge.
But for me, I tend to drop files in different computers and such, so I haven’t lost anything critical, the thing didn’t even know what Solidworks was, so those files weren’t touched, I’ve updated the virus and malware stuff and I’m stripping the files to long term storage and cleaning up. And writing a series of posts on all this. All is not lost.
LikeLike
I’m sorry to hear about your computer difficulties.
Though this probably isn’t applicable to restoring your files, and though this might not have prevented the attack in this case, here is something I’ve been doing recently for security:
I’ve been browsing the web using a virtual machine set up with virtualbox. I create a small (50 GB) virtual hard drive and install linux on the virtual PC, and browse the internet through browsers on the virtual machine. I’m pretty sure no virus writer has gotten clever enough to break into a virtual PC, then break the virtual machine, then break the host computer yet. I can have the virtual PC (with all the usual linux utilities) available while I’m working with MS Office/etc on Windows 7.
Sorry to hear about your troubles.
LikeLike
Your understanding of cryptography in general and public key encryption in particular is completely wrong.
“See the key vulnerability of any encryption scheme is the fact that the original has to be clear. if somebody has an original copy in clear, encryption doesn’t work.”
“There’s also the fact that the greatest weakness in encryption is that there has to be retrievable information and access to clear copy means that the key is right there.”
What you are talking about here is a known plaintext attack, it worked on the encryption used in the 1500s, it was part of the process of breaking the encryption used in world war 2, but in 2016 it’s pretty much a solved problem. No modern crypto algorithm is vulnerable to a known plaintext attack. Having a copy of the original file in no way exposes any information about the key.
Also, just because a very small small handful of ransomware hosts have been taken down and decrypt tools created, is in no way a guarantee that they all will. “Even if the decryption isn’t available now, it more than likely will be soon” is a massive exaggeration at best.
LikeLike
From what I’ve been able to find, each and every new version of these ransomware tools has been cracked. and I never said that the attack was going to be plain text, all by itself. I’m fully aware that plain text would not work on an algorithmic encryption. But, what happens if you have the original file(plaintext, though the files I’m thinking of are not text), the public key and the encrypted file, then the problem becomes a one equation, one unknown and that is solvable. Kapersky seems to think it is anyway. Since I can’t afford to pay the ransom, the point is moot anyway. So waiting thinking up different lines of attack are the only thing I can do.
LikeLike
“From what I’ve been able to find, each and every new version of these ransomware tools has been cracked”
Look harder, there are hundreds if not thousands of ransomware variants out there, a few dozen have had decryption tools released.
Plaintext attack doesn’t mean the content of the file is text, it means that you possess an unencrypted copy of some of the encrypted data.
“But, what happens if you have the original file(plaintext, though the files I’m thinking of are not text), the public key and the encrypted file, then the problem becomes a one equation, one unknown and that is solvable.”
Technically, if you are talking public key encryption (like RSA), then just possessing the public key is enough to calculate the private key, the problem is it will take all of the computers in the world longer than the age of the universe to do it using current knowledge. Possessing an encrypted file and it’s plaintext partner doesn’t give you any additional information or make it any easier to determine the private key. That is what resistant to plaintext attacks is all about.
If we are talking about symmetric cyphers, then there is no public key and you would only possess the plaintext and the cyphertext data, and again to the best of our knowledge, modern algorithms like AES do not leak any information as a result of this. You cannot use the plaintext to determine the key. You could use it to verify that you have the correct key during a brute force search of the keyspace, but again, all the computers, age of the universe, etc.
LikeLike
And why should I believe you. You can’t even use your name or a real email address. What’s your expertise in this area? Right now your having no credibility with me whatsoever. Or are you too afraid to use your real name and tell me your experience?
LikeLike
You shouldn’t believe me. You should do your own research and actually understand the subject especially if you are going to try to educate others.
Here are some starting points.
https://en.wikipedia.org/wiki/Known-plaintext_attack
https://en.wikipedia.org/wiki/Public-key_cryptography
https://en.wikipedia.org/wiki/Integer_factorization
Yes, I am afraid to use my real name. Not because what I’ve said here is wrong or in some way harmful to me, but because I value my privacy online and anything that involves sharing private information reduces the level of privacy I enjoy. A lot of people in the security industry are reluctant to share personal details, especially if it is for no good reason. Look at any security conference schedule and you will see people presenting research under pseudonyms and aliases. Adding my name and email address offers no benefits to you or anyone else and only serves to increase my exposure. Why should I trust you with more information about me than what you actually require?
If pointing out that I’m not willing to share my email address to anyone who asks is the strongest argument you have against what I’ve said, you’re not on a terribly strong footing.
LikeLike
Give me more than the wikis I looked dup earlier this week. And if you are in security, you might realize that you may not be anonymous as you think. I hope you aren’t posting from your employer in Sydney. Note that that took me seconds. Still I’ve seen nothing that gives any confidence that you have a clue about any of this.
LikeLike
So you’re sharing details about what I filled in to the email field which you claim won’t be made public, and now you are releasing information about my location and you wonder why I don’t trust you enough to give you even more private information? You are the reason that people like me don’t like sharing information, you abuse what info you have to try to make up for the fact that you can’t understand the explanations that you, apparently, read (how did you think that plaintext referred to text files if you had already read about plaintext attacks? and are you still claiming that RSA is susceptible to known-plaintext cryptoanalysis?).
LikeLike
Do you want some cheese with that whine. Actually you didn’t fill out the email block. I didn’t need that. I will leave it to you to figure out how I did find out where you were and wonder just how much else I found out. And names aren’t usually private. The only people who feel the need to hide are trolls or crooks. You don’t seem to be a crooks so I guess you are a troll.
LikeLike